Conduit Executive Summary
Updated Jan 16, 2025
What is Conduit Network?
Conduit Network is a computer network designed with decentralized opinions and a robust rewards program. Conduit Network provides a rich set of semantics and protocols designed to facilitate and foster mutualized economic activity in which all parties involved experience the benefits of the networks success. The design of Conduit Network is based on three key tenets:
- Cost Reduction
- Mutual Benefit
- Decentralization
Cost Reduction
A key tenet of the design of Conduit Network is cost reduction and maximizing the amount of value transferred in an exchange. Many of the protocols of the Conduit Network are rooted in the science of supply chains where standardization of practices and centers of excellence are established, and redundancies are eliminated.
Mutual Benefit
Conduit protocols draw on the incentivization models of supply chains and co-ops where aspects of employee owner and customer owner are evident. All participants of the Conduit Network are owners of the Conduit Network in some capacity, which creates a reality where "a rising tide raises all ships" and the benefit of your competitor ultimately benefits you (and everyone).
Decentralization
Conduit Network sees decentralization as a means to two ends: self-sovereignty and efficiency. In many circumstances, peer-to-peer interaction reduces friction (often materialized in loss of value) and eliminates interference vectors. Decentralization allows the individual to take responsibility for their own property, which ultimately provides liberty. Many Conduit protocols are designed to be "thin services" that promote and facilitate peer-to-peer interaction and allow the individual parties to request and disclose information.
How to get involved
Here is a high-level breakdown of how the current Conduit Network products interact with the Conduit Rewards System. If you would like to find out more about how to purchase our products, please visit our Web 3 Shop or Fiat Shop.
Join us on the following platforms to stay up to date and participate in our growing community
Conduit Hardware
Updated Jan 16, 2025
Conduit manufactures hardware for the purpose of providing the necessary hardware security and network topology to fulfill the vision of the Conduit Network. In particular, Conduit has taken on the responsibility of manufacturing the first hardware devices to meet the High Trust hardware security requirements called Security Modules.
Conduit offers a bundle of hardware called the Conduit Core, which contains three devices that are essential to the Conduit Network. These devices are:
- The Connectivity Module
- The Security Module
- The Compute Module
Together, these devices enable much of the capability of the Conduit Network as well as enable a wide set of compensation models. The Conduit Core is intended for personal and small to medium sized business use. For the workloads of larger businesses and data centers reach out to find out about Conduit Server, or if you would like to find out about how Conduit can support your unique business or project contact us about Domain Specific Solutions.
For certain types of network activity, Conduit also allows participants to use computer hardware of their choice with a qualifying operating system and operational license. (See Conduit Node0 License).
Connectivity Module
Updated Jan 16, 2025
Conduit manufactures a Connectivity Module that can act as part of the Conduit Core or as a stand-alone module. The Connectivity Module is designed to act as the primary network connection device for the Conduit Core as well as being a full-fledged home or small office Wi-Fi router. In addition to providing Wi-Fi the Connectivity Module also serves as the bus controller for the Conduit Core module stack and has a visual display for reporting activities and metrics for the connected devices and the Conduit Network. The Connectivity Module and associated bus will also support the addition of a separate module to provide 5G network connectivity as a primary or redundant internet connection.
The Founders Edition Connectivity Module has the following estimated specifications:
| Name | Value |
|---|---|
| Wi-Fi Protocol | Wi-Fi 7 |
| Bands | 2.4GHz, 5GHz, 6GHz |
| Standards | 802.11 a/b/g/n/ac/ax/be |
| Maximum Speed* | 5.8Gbps |
| Mesh Capable | Yes |
| Available 5G connectivity | Yes |
| *Theoretical maximum speed |
Security Module
Updated Jan 16, 2025
Conduit manufactures a Security Module that can act as part of the Conduit Core or as a stand-alone module. The Conduit Security Module is designed to solve the problem of physical device security by manufacturing the device securely, rather than having to physically secure the environment it is in. This is essential to be able to secure edge computing and ultimately, decentralization. The Conduit Security Module is manufactured using the most secure manufacturing processes available, while keeping the price commercially feasible. Physical tampering of the computer in the Security Module is nearly impossible, even in extreme temperature scenarios, without destroying or making the device inoperable.
At the time of pre-sale, the Conduit Security Module will be the only High Trust device available for purchase. Therefore, the network of these devices will be responsible for running the Conduit Secure Core Services and entitled to the compensation for doing so.
The Founders Edition Security Module has the following estimated specifications:
| Name | Value |
|---|---|
| CPU Clock | 4.2GHz |
| Cores | 4 (8 Threads) |
| TDP | 25W |
| RAM | 16GB |
| Storage | 512GB |
Compute Module
Conduit manufactures a Compute Module that can operate as a part of the Conduit Core or stand alone. The Compute Module is a computer designed to bring server level computing power into a small form factor suitable for home or office deployment. Coupled with a Node0 License, the Conduit Compute Module is intended to operate as a Worker Node with a compute cloud Smart Meter on the Conduit Network.
The compute resources of the Compute Module can be offered to the Conduit Cloud for lease or leased directly by the owner of the Compute Module for their own use (web hosting, running containers, personal cloud backup, and more).
The Compute Module is not intended to be used as a traditional personal computer but rather as an edge node for the Conduit Network.
The Founders Edition Compute Module has the following estimated specifications:
| Name | Value |
|---|---|
| CPU Clock | 3.7GHz |
| Cores | 16 |
| RAM | 64 GB |
| Storage | 4TB |
| Connectivity | Thunderbolt 4/USB 4.0, Ethernet (RJ-45) |
Hardware Trust Levels
A core tenet of the Conduit Network is to decentralize the internet, enabling clusters of nodes to operate on the edge, rather than in large centralized data centers run by "Big Tech". To do this, the benefits of physical security provided at data centers must be achieved in a different way. Conduit Network has defined four hardware trust levels to help consumers understand different tiers of security for decentralized and sovereignly operated hardware. Conduit has also taken on the responsibility for producing the first High Trust hardware for running Core Security Nodes with the Security Module included in the Conduit Core. Following are the hardware Trust Levels for Conduit Network:
- Low Trust: appropriate for use only when there is virtually no value lost, should the device be compromised - or gaining access to or changing the information it contains or produces. Shared public information that can be easily regenerated is a good example. Any hardware system can be considered a Low Trust Node. In fact, all non-verified Nodes in the Network are considered Low Trust Nodes until proven differently. This means that any device already owned or in use by anyone on the internet can be considered and used as a Low Trust Node. The Conduit infrastructure Ecosystem websites and apps do not offer any pre-configured Low Trust Nodes, as their use is not encouraged by the Network. However, every piece of hardware connected to the internet today, unless certified to a higher standard, every cloud computing environment, is considered Low Trust.
- Standard Trust: appropriate for use where there is low value to someone gaining unauthorized access, or for use where there may be economic loss, but which would not be significant – either in individual cases or the aggregate. Standard Trust Nodes may be considered Enhanced Trust Nodes when they exist in environments that have high physical and connectivity protection, as in secure data centers or in private networks not connected to the internet. Standard Trust Nodes can be supplied by many commodity hardware providers. Even legacy hardware that Network Participants already own may qualify for use as a Standard Trust Node. Standard Trust Nodes can be acquired directly from their suppliers and configured to operate within the Network by installing a Worker Node OS by purchasing a Node0 License. Also, a limited list of pre-configured Standard Trust Nodes are available for purchase via the Conduit infrastructure Ecosystem websites and apps. These come with the Worker Node OS preinstalled and a Node0 License.
- Enhanced Trust: represents a compromise between Standard Trust and High Trust that attempts to find the sweet spot between cost and the friction of use versus the skill or economic cost of breaching security or violating trust. Enhanced Trust Nodes are only available from a list of qualifying hardware device manufacturers from vetted third parties. Enhanced Trust Nodes can be purchased directly from their suppliers, and can be configured to operate within the Network by buying a Node0 License – or purchased pre-configured through the Conduit infrastructure Ecosystem, which comes with the Worker Node OS preinstalled and a Node0 license.
- High Trust: appropriate for use in the most demanding trustless security environments, including critical banking, nation-state, and utilities infrastructure. These Nodes can only be purchased through licensed Syndicates (a Network version of a DAO) within the infrastructure Ecosystem. These Syndicates must demonstrate that they maintain a fully audited supply chain that provides full provenance for all components. All components deemed to pose a quantifiable risk must also come from Members of a licensed Syndicate within the infrastructure Ecosystem. All hardware, OS and software for High Trust Nodes are designed by Conduit, and are only manufactured by licensed Parties who use approved suppliers for components. Software components can only be created and modified by licensed Parties and must be audited by licensed Parties. All hardware for High Trust Nodes that run Secure Core Services must be NIST rated to comply with the FIPS 140-2 (level 3) standards or higher.
The entire supply chain for High Trust Nodes must ensure provenance and auditable history of each component. Any party who wishes to participate in building components for High Trust Nodes must go through a rigorous training process, risk assessment, and submit to regular audit processes, as well as agreeing to join a Syndicate that places the right to all IP used within a Network trust. Therefore, High Trust Nodes for use in the Network are only available through the Conduit infrastructure Ecosystem and must be purchased through Network websites or apps.
Conduit Software
Conduit produces software that supports the security paradigms it presents, facilitates the decentralized Conduit Cloud, and implements the Conduit Rewards System. Following are some of the key software components produced by Conduit:
Secure Core Services
Conduit maintains a set of software services that enable core functionality to the Conduit Network called Secure Core Services. Conduit Secure Core Services run exclusively on High Trust hardware devices like the Conduit Security Module. Following is overview of the Secure Core Services:
- Accounting
- Accounting - Rollup level accounting, order and fulfillment resources.
- Temporal Ledgers - Party, inventory and accounting entity ledgers.
- Secure Storage - Party keys and secret information.
- Wallet Accounts - Manage the wallet accounts for all accounting entities.
- Data
- Database - Database services
- File System - Manage files and folders for shared access to files.
- Replication - Data replication, distribution and consensus.
- Messaging - Publish and subscribe message queues
- Financial
- Blockchain/DLT - Interfaces, bridges and tokenization and de-tokenization on demand.
- Payments - All transfers of value, paywalls, exchange and card issuing / processing.
- Registries - Digital asset management
- Treasuries - Assets custodian via regulator entities and compliance.
- Identity
- Authentication - Ensure identity for actors is known and appropriately authenticated.
- Authority - Ensure actors only access resources to which they have legal authority.
- Profile - Manage the profile and credentials of all parties (KYC, preferences, etc.).
- Resource - Manage the identity, authentication and verification of all resources.
- Resource
- Allocation - Resource allocation and use, capacity and gaps assessment.
- Billing - The calculation of charges for all resource use, sale and transfer.
- Utilization - Manage resource configuration and location to maximize value.
- Directory - Resource name services and routing needed to optimize provisioning.
Worker Node OS
Updated Apr 1, 2025
Conduit Network maintains a Linux based immutable operating system image that is deployed to Worker Nodes. This operating system implements and maintains the security specifications and authorization models employed by the Conduit Network. A hash of this image is used in security procedures when Worker Nodes are interacting with Security Modules. This operating system is a prerequisite for Worker Nodes to operate on the Conduit Network and for participating in the Conduit Rewards System.
Smart Meters
Conduit Smart Meters are used to measure resource events (change, use, etc.) either on or off network. Smart Meters are deployed as a part of the Worker Node OS, measure and monitor resources, and interface with a Security Module to store data in Conduit Temporal Ledgers.
Smart Meters support a Predicate language that is used to define significant events and measurements that are communicated via a cryptographic proof to Network Message Queues. From a high level, this language allows developers to define when:
- A significant event occurs within a workflow that will trigger a state transition,
- A notification event occurs for human or machine
- A periodic event occurs with the measurements or metrics related to resource for that period, or
- A heartbeat that represents a time interval passing without a significant event occurring.
Predicates support the ability to transfer information about an event or measurement to Message Queue subscribers in the form of a Predicate Proof. A Predicate Proof supports both zero knowledge proofs or transparent information accessible by anyone with authority to access the Predicate Proof.
All Smart Meters perform two requisite functions:
- The creation of Predicate Proofs upon a Predicate detecting a significant event, and
- Providing billing information for use, sale or transfer of a Resource the Smart Meter monitors or measures to a Security Module to calculate the charge and do the Billing and Settlement.
Smart Meters are designed to deal with following types of events:
- Calendar – events based on time of day, date/time, day in a period, holiday, etc.,
- Duration – events related to elapsed time; minutes, hours, days, etc.,
- Message – based on the call of an API, receipt of a message or the addition, change or deleting of a file,
- Polling – the periodic call of an API, script, URI or process that provides a return, and
- Signal – events such as a call to API supported by the specific type of Smart Meter.
Smart Meters are written to work for a specific type of Resource or class of Resource. They can be built to work with special devices or to support a particular system. Examples include IoT temperature devices, vehicle operations sensors, point of sale devices, credit card machines, bank account balances for a specific bank, inventory control systems, etc. There are theoretically an infinite number of Smart Meters that can be created because there are an infinite number of Resources that could be controlled by the Conduit Network.
The Conduit Network provides a set of Smart Meters for Worker Nodes and some others for common use cases, primarily as examples. However, Smart Meters are intended to be created by the Conduit Network community.
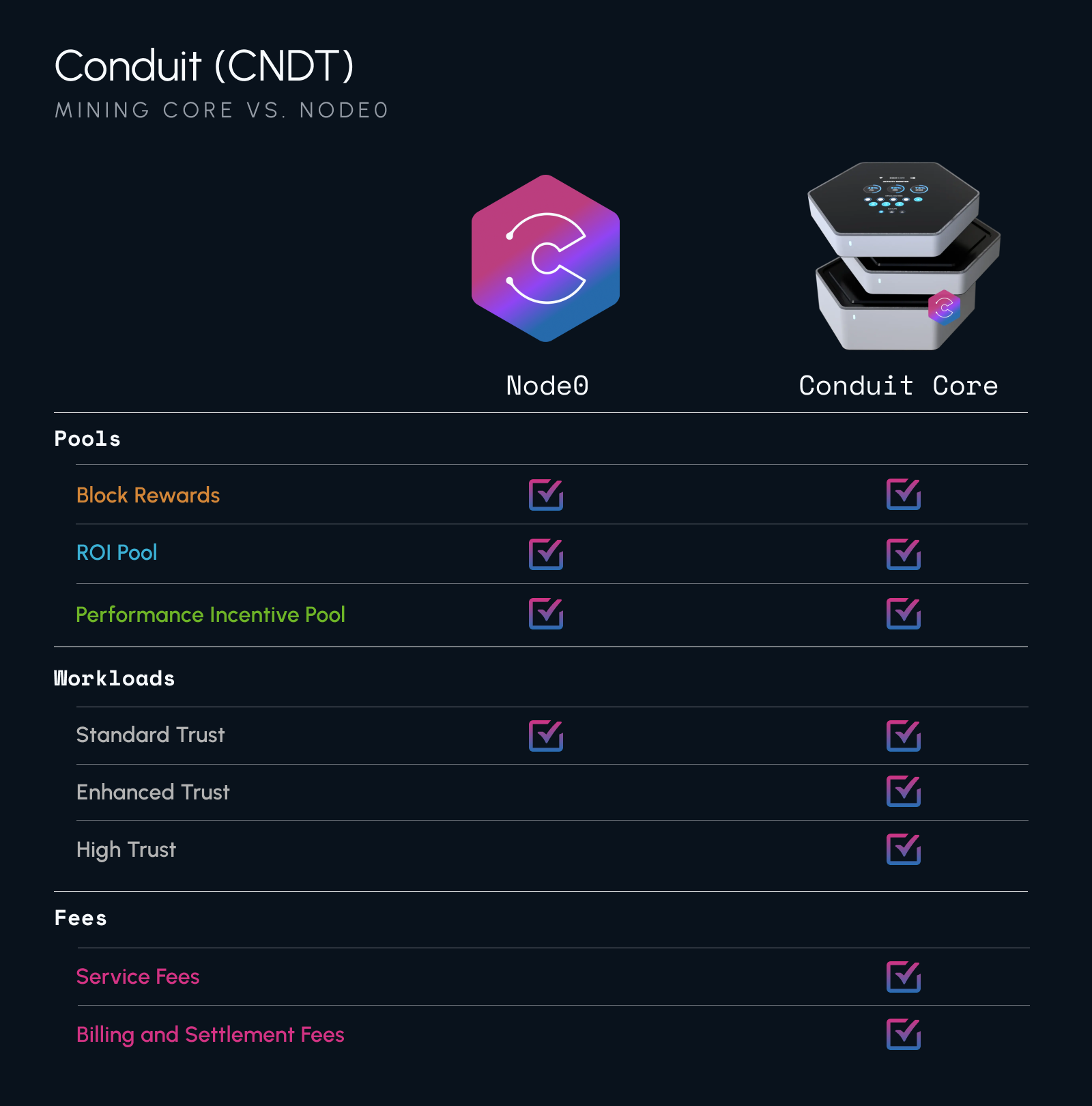
Node0 License
Conduit offers a license for operating computer hardware not manufactured by Conduit on the Conduit Network. This license, plus a verified version of the Conduit Worker Node OS are prerequisites for operating on the Conduit Network and participating in the Conduit Rewards System.
Conduit Cloud Introduction
All computer networks are built on just that, computers, and Conduit Network is no different. Computers in the Conduit Network are categorized as different types of Nodes based on their function and their Trust Level. Here we will illustrate a very basic example of these different Node types in action.
First, let us establish the Parties in the scenario:
- Sammy has a small business and is interested in publishing a website on WordPress.
- Marcel is the operator of a Conduit Compute Module which is a type of Worker Node and has opted to let the Conduit Network manage and optimize the deployments on his node. (Marcel could choose to manage his Compute Module more directly, but that is a different topic.)
- Another party not considered in detail in this scenario operates a marketplace website that helps connect hosting buyers with hosts.
Sammy finds a WordPress hosting option from a Conduit Network marketplace website and decides to purchase hosting. This initiates Sammy's Security Module to place an order for hosting service based on what was described on the marketplace website. The Conduit Network finds a host matching the advertised requirements (Marcel's Compute Module). Marcel's Security Module picks up the order and starts provisioning the resources from his Compute Module. In this case, a container-based deployment of WordPress is deployed to Marcel's Compute Module and Sammy is sent credentials to manage the new WordPress site. (Note: many things in this example have been trivialized to focus on how these parties interact—topics like uptime, redundancy, backup and networking will be covered in other documentation.)

Worker Nodes
A Worker Node on the Conduit Network is the connective tissue between the Conduit Service Layer and tangible resources (bandwidth, compute, any measurable asset with value) via a Smart Meter that can measure changes on that resource. Joining a qualifying computer to the Conduit Network with a valid Conduit Node0 License will cause the machine to be fully managed by the Conduit Network (with the ability to assign it specific work or offer it to meet network demand) and enable that computer to participate in Conduit Mining activities. Assigned work will earn compensation for fulfilling work measured by Smart Meters via a Security Module for Billing and Settlement.
A common deployment of a Worker Node would be a Compute Module that offers the compute resources of the computer that it is deployed on to be fully allocated by the Conduit Network. In this scenario the Conduit Network would provision the machine to run the Worker Node OS, which includes a hypervisor. Then, based on demand of the Network, decide how to use those resources. This could be to add them to a cluster for containerized workloads or set up to be a Virtual Private Server (VPS), or a combination of both.
Worker Nodes are classified by the Smart Meter(s) they run as well as the Trust Level they qualify for. Market price for work fulfillment will increase with Trust Level, due to the overhead of operating a Worker Node at a higher Trust Level.
Security Modules
Security Modules in the Conduit Network are responsible for running the Conduit Secure Core Services. At a high level these services include:
- Accounting
- Data
- Financial
- Identity
- Resource
Security Modules are always built with hardware that meets the High Trust hardware specification. The Conduit Core Founders Edition contains a Security Module. More information about the Secure Core Services can be found in the Conduit Software Secure Node Services Page.
Conduit Rewards System
Conduit implements a multifaceted rewards system for many different types of participation in the network, with the goal to create a secure decentralized network for both Web 2 and Web 3, owned by its operators, creators and users.
The Conduit Rewards System adopts the term "mining" as aspects of the mechanics of how CNDT tokens are released resemble proof-of-work. A more accurate way of describing how tokens are released in the Conduit Network is "proof of economic activity". Conduit Network measures economic activity by a metric called CROP, which like "gas", is collected on every economic transaction, but unlike "gas", is used to Mine CNDT, the native token of the Conduit Network.
Mining on the Conduit Network is governed by a block release schedule that is divided into Phases representing thresholds of overall Conduit Network economic activity (think GDP), with a predetermined number of Blocks per phase. Each Block contains a predetermined amount of CNDT, based on which Phase the block is in.
When blocks are Mined by users, the released CNDT is distributed according to a set of distribution tables, often called "pools". These pools are designed to simultaneously reward parties for participating economically (contributing CROP), support the network, and incentivize additional economic and network activity. Distribution tables can be and often are nested and can be subject to Conduit Network protocols and governance, as well as contracts between parties. The following image is an example of the top-level distribution pool for the Conduit Network.
This serves as a high-level overview of how the Conduit Network Rewards System works. Additional pages of documentation will explore the topics of CROP, Mining, and Block Distribution.
Mining
TLDR; Mining on the Conduit Network is a race to meet thresholds of economic activity. More economic activity by a Party means more Mining opportunity.
Overview
Mining on the Conduit Network is done any time a CROP contribution is made on an economic transaction by participating parties. All economic transactions in the Conduit Network have a requisite CROP contribution of 2% of the transaction value, but parties participating in the transaction can voluntarily contribute more CROP up to the value of the transaction. For people familiar with blockchain tokenomics, this can be thought of as a hybrid of gas fees, staking, and block mining. All CROP contributions are placed in a distribution pool that is designed to support the Conduit Network and its participants, as well as incentivize economic activity within the network. CROP is like a gas fee because some of the distribution pool is allocated to compensating parties for running the network itself. It is like staking because at a transactional level it requires Parties to have some "skin in the game". Finally, CROP is like mining because blocks of CNDT are released to parties when economic activity thresholds are met.
Mining Mechanics
Every Party in the Conduit Network has a CROP Ledger which tracks the CROP contributions of that Party. The primary function of a CROP Ledger as it pertains to Mining is to keep a running total of CROP contributions for a Party in order to see if a Block Threshold has been met by the Party. When a Party meets a Block Threshold for a given Phase, they "win" the corresponding Block of CNDT.
Blocks of CNDT are grouped into Phases, which change the amount of CNDT in blocks as the total economic activity increases (by measuring total CROP contribution) as well as the number of Blocks in a Phase. The goal of these Phase changes is to distribute Block wins more widely across Participants as the overall economic activity of the Network increases.
Mining with a Security Module
Security Modules are eligible to receive rewards from both Distribution Pools (based on all Conduit Network economic activity) and from direct mining (Block Rewards) based on CROP contributions.
Distribution Pool Rewards
The Distribution Pools that a Security Module can receive from are the Performance Incentive Pool and the ROI pool. The Party that owns the Security Module is entitled to allocations from the ROI Distribution pool until the value used to acquire the Security Module has been recouped. The Party that owns the Security Module is also entitled to allocations from the Performance Incentive Pool, if they meet prescribed Conduit Network service requirements (up-time, bandwidth, etc.).
Mining with Fees
Security Modules also Mine from the Block Rewards Pool as they are uniquely able to Mine with the Service Fees and Billing and Settlement Fees they collect, which are automatically converted to CROP contributions for the operating Party. A normal scenario for a Security Module could be that they act as the Billing and Settlement node for around 100 Parties (i.e. family members' transactions, their own and their friends' and families' business transactions) from which they collect Service Fees and Billing and Settlement Fees as CROP contributions, in addition to their own personal transactions.
Mining with a Node0 License (Worker Node)
Conduit Network supports running Worker Nodes with a Node0 License as a means to provide resources to the network and Mine CNDT.
Distribution Pool Rewards
The Distribution Pools that a Worker Node with an attached Node0 License can receive from are the Performance Incentive Pool and the ROI Pool. The Party that owns the Worker Node is entitled to allocations from the ROI Distribution Pool until the value used to acquire the Node0 License has been recouped. The Party that owns the Worker Node and attached Node0 License is also entitled to allocations from the Performance Incentive Pool, if they meet prescribed Conduit Network service requirements (up-time, bandwidth, resource availability, etc.).
Mining Block Rewards
Worker Nodes on the Conduit Network run Smart Meters that measure Resources which are sold as a good or service on the network. In the case of the Compute Module, the Resource being sold is the compute on the same device which is running the Worker Node OS and requisite Smart Meter; a similar scenario can be implemented on existing qualifying hardware. When the Party that owns and operates the Worker Node sells these resources to another Party on the network, they are required to contribute at least 2% of the transaction value in CROP. (Remember, the more CROP contributed by a Party, the more blocks they will Mine)
Notes about CROP Contributions
CROP contributions can be made by each of the Parties in a transaction (example: buyers and sellers). So in a $1000 transaction, the minimum 2% would be contributed by the seller, +$20 would be recognized in the seller CROP contribution ledger. If the buying Party also wanted to mine on the transaction, they may, recognizing the amount contributed in the buyer's CROP contribution ledger, up to the value of the transaction itself.
It is worth noting that a 2% CROP contribution is the minimum required by the network, but the Party that owns and operates the Worker Node may choose to increase this contribution to increase mining potential. (There may be circumstances where it is more lucrative to contribute the value earned in a sale as CROP than to keep the value itself.).
It may help to think about the seller CROP contribution as "gas" on a blockchain network, and the buyer CROP contribution as a "tip" on the transaction. Both of these activities qualify as Mining on the Conduit Network, and these contributions are tracked in the respective Party's CROP contribution ledger.
Mining as a Participant
The Conduit Network supports mining without even running a Node on the network. Participants in the Conduit Network may engage in Mining CNDT any time they participate in an in-network transaction if they make a CROP contribution on that transaction. This can be thought of like "tipping" as it is additional value transferred on top of the transaction value, although the benefit goes to the Party making the tip, because the "tip" amount is recognized in the buyer CROP contribution ledger.
Bitcoin and Conduit Mining Comparison
Both Conduit and Bitcoin use the term "mining." The following table helps show how the mining process is different between the two.
| Area | Bitcoin Mining | Conduit Mining |
|---|---|---|
| Chain | One common replicated chain | A graph network of DLTs |
| Mining Algorithm | Proof of Work | Proof of Economic Activity |
| Mining Goal | Mining based on first mine to reach a mathematical goal of a hash that fits a pattern | Mining based on next time a Party reaches an economic goal of having purchased a certain amount of rewards for all Conduit Network Participants. |
| Race Between | All mines (only one wins) | Each Party mines on its own |
| Block Verified | After majority of nodes verify | After registry nodes issue CNDT |
| Speed to confirm block | Approximately 10 minutes | Approximately 1 second |
| Max Block Size | 1 Megabyte | N/A |
| Energy need per token | At least 143,000 kWh | Average of 78 kWh (1,833 times less energy) |
| Halfing Phases | 6 | 60 |
| Time of each phase | ~4 years | Takes longer for subsequent phases |
| New phase based on | Block count | Doubling of the economic activity |
| Tokens at genesis block | 50 | 16,777,216 |
| Blocks per phase | 210,000 per phase | Doubles each phase (starting at 1) |
| Distribution of mined tokens | Only one mine owner wins | 33.34% goes to mine owner, the rest goes to network pools (see distribution table for detail) |
| Max Tokens | 21M Bitcoin | ~1B Conduit (1,006,632,960) |
| Time to mine all tokens | 2.5 decades | A century or more |
| Economic Activity | Transfer of value using bitcoin | Use, sale or transfer of cloud based Resources (assets, IP, goods and services) |
| Use | Transferring value | Running decentralized cloud for web 2 & 3 |
| Max transaction speed | 7 per second for network | Theoretically limited only by number of Nodes. 6 per second per Quad Security Modules (Network speed is based on how many Security Module verify a transaction and geo diversity, network speed scales linearly to Security Module count) |
| Economics based on | Only one winner | All active contributors win, plus the miner gets a bonus. |
| Economics Incentivize | Centralization of faster mines | Decentralization of all mines into the hands of people |
| Mine owners | Can be anyone | Only KYC’d individuals or pools of individuals |
Mining Phases Table
Following is a table that describes the Mining Phases of the Conduit Network including the amount of CROP required to Mine a Block and the number of Blocks per Phase.
| Phase | CROP to Mine Block (in $USD) | CNDT per $USD of CROP | Cumulative CNDT mined | Cumulative $USD contributed to CROP | CROP ($USD) per Block | Blocks per Phase | Cumulative Blocks Released | CNDT per Block |
|---|---|---|---|---|---|---|---|---|
| 1 | 1 | 16,777,216 | 16,777,216 | 1 | 1 | 1 | 1 | 16,777,216 |
| 2 | 2 | 8,388,608 | 33,554,432 | 3 | 2 | 1 | 2 | 16,777,216 |
| 3 | 4 | 4,194,304 | 50,331,648 | 7 | 4 | 1 | 3 | 16,777,216 |
| 4 | 8 | 2,097,152 | 67,108,864 | 15 | 8 | 1 | 4 | 16,777,216 |
| 5 | 16 | 1,048,576 | 83,886,080 | 31 | 16 | 1 | 5 | 16,777,216 |
| 6 | 32 | 524,288 | 100,663,296 | 63 | 32 | 1 | 6 | 16,777,216 |
| 7 | 64 | 262,144 | 117,440,512 | 127 | 64 | 1 | 7 | 16,777,216 |
| 8 | 128 | 131,072 | 134,217,728 | 255 | 128 | 1 | 8 | 16,777,216 |
| 9 | 256 | 65,536 | 150,994,944 | 511 | 256 | 1 | 9 | 16,777,216 |
| 10 | 512 | 32,768 | 167,772,160 | 1,023 | 512 | 1 | 10 | 16,777,216 |
| 11 | 1,024 | 16,384 | 184,549,376 | 2,047 | 1,024 | 1 | 11 | 16,777,216 |
| 12 | 2,048 | 8,192 | 201,326,592 | 4,095 | 2,048 | 1 | 12 | 16,777,216 |
| 13 | 4,096 | 4,096 | 218,103,808 | 8,191 | 2,048 | 2 | 14 | 8,388,608 |
| 14 | 8,192 | 2,048 | 234,881,024 | 16,383 | 2,048 | 4 | 18 | 4,194,304 |
| 15 | 16,384 | 1,024 | 251,658,240 | 32,767 | 2,048 | 8 | 26 | 2,097,152 |
| 16 | 32,768 | 512 | 268,435,456 | 65,535 | 2,048 | 16 | 42 | 1,048,576 |
| 17 | 65,536 | 256 | 285,212,672 | 131,071 | 2,048 | 32 | 74 | 524,288 |
| 18 | 131,072 | 128 | 301,989,888 | 262,143 | 2,048 | 64 | 138 | 262,144 |
| 19 | 262,144 | 64 | 318,767,104 | 524,287 | 2,048 | 128 | 266 | 131,072 |
| 20 | 524,288 | 32 | 335,544,320 | 1,048,575 | 2,048 | 256 | 522 | 65,536 |
| 21 | 1,048,576 | 16 | 352,321,536 | 2,097,151 | 2,048 | 512 | 1,034 | 32,768 |
| 22 | 2,097,152 | 8 | 369,098,752 | 4,194,303 | 2,048 | 1,024 | 2,058 | 16,384 |
| 23 | 4,194,304 | 4 | 385,875,968 | 8,388,607 | 2,048 | 2,048 | 4,106 | 8,192 |
| 24 | 8,388,608 | 2 | 402,653,184 | 16,777,215 | 4,096 | 2,048 | 6,154 | 8,192 |
| 25 | 16,777,216 | 1 | 419,430,400 | 33,554,431 | 4,096 | 4,096 | 10,250 | 4,096 |
| 26 | 33,554,432 | 0.5 | 436,207,616 | 67,108,863 | 4,096 | 8,192 | 18,442 | 2,048 |
| 27 | 67,108,864 | 0.25 | 452,984,832 | 134,217,727 | 4,096 | 16,384 | 34,826 | 1,024 |
| 28 | 134,217,728 | 0.125 | 469,762,048 | 268,435,455 | 4,096 | 32,768 | 67,594 | 512 |
| 29 | 268,435,456 | 0.0625 | 486,539,264 | 536,870,911 | 4,096 | 65,536 | 133,130 | 256 |
| 30 | 536,870,912 | 0.03125 | 503,316,480 | 1,073,741,823 | 4,096 | 131,072 | 264,202 | 128 |
| 31 | 1,073,741,824 | 0.015625 | 520,093,696 | 2,147,483,647 | 4,096 | 262,144 | 526,346 | 64 |
| 32 | 2,147,483,648 | 0.0078125 | 536,870,912 | 4,294,967,295 | 4,096 | 524,288 | 1,050,634 | 32 |
| 33 | 4,294,967,296 | 0.00390625 | 553,648,128 | 8,589,934,591 | 4,096 | 1,048,576 | 2,099,210 | 16 |
| 34 | 8,589,934,592 | 0.001953125 | 570,425,344 | 17,179,869,183 | 4,096 | 2,097,152 | 4,196,362 | 8 |
| 35 | 17,179,869,184 | 0.0009765625 | 587,202,560 | 34,359,738,367 | 4,096 | 4,194,304 | 8,390,666 | 4 |
| 36 | 34,359,738,368 | 0.00048828125 | 603,979,776 | 68,719,476,735 | 8,192 | 4,194,304 | 12,584,970 | 4 |
| 37 | 68,719,476,736 | 0.000244140625 | 620,756,992 | 137,438,953,471 | 8,192 | 8,388,608 | 20,973,578 | 2 |
| 38 | 137,438,953,472 | 0.0001220703125 | 637,534,208 | 274,877,906,943 | 8,192 | 16,777,216 | 37,750,794 | 1 |
| 39 | 274,877,906,944 | 0.00006103515625 | 654,311,424 | 549,755,813,887 | 8,192 | 33,554,432 | 71,305,226 | 0.5 |
| 40 | 549,755,813,888 | 0.00003051757813 | 671,088,640 | 1,099,511,627,775 | 8,192 | 67,108,864 | 138,414,090 | 0.25 |
| 41 | 1,099,511,627,776 | 0.00001525878906 | 687,865,856 | 2,199,023,255,551 | 8,192 | 134,217,728 | 272,631,818 | 0.125 |
| 42 | 2,199,023,255,552 | 0.000007629394531 | 704,643,072 | 4,398,046,511,103 | 8,192 | 268,435,456 | 541,067,274 | 0.0625 |
| 43 | 4,398,046,511,104 | 0.000003814697266 | 721,420,288 | 8,796,093,022,207 | 8,192 | 536,870,912 | 1,077,938,186 | 0.03125 |
| 44 | 8,796,093,022,208 | 0.000001907348633 | 738,197,504 | 17,592,186,044,415 | 8,192 | 1,073,741,824 | 2,151,680,010 | 0.015625 |
| 45 | 17,592,186,044,416 | 0.0000009536743164 | 754,974,720 | 35,184,372,088,831 | 8,192 | 2,147,483,648 | 4,299,163,658 | 0.0078125 |
| 46 | 35,184,372,088,832 | 0.0000004768371582 | 771,751,936 | 70,368,744,177,663 | 8,192 | 4,294,967,296 | 8,594,130,954 | 0.00390625 |
| 47 | 70,368,744,177,664 | 0.0000002384185791 | 788,529,152 | 140,737,488,355,327 | 8,192 | 8,589,934,592 | 17,184,065,546 | 0.001953125 |
| 48 | 140,737,488,355,328 | 0.0000001192092896 | 805,306,368 | 281,474,976,710,655 | 16,384 | 8,589,934,592 | 25,774,000,138 | 0.0019531250 |
| 49 | 281,474,976,710,656 | 0.00000005960464478 | 822,083,584 | 562,949,953,421,311 | 16,384 | 17,179,869,184 | 42,953,869,322 | 0.0009765625 |
| 50 | 562,949,953,421,312 | 0.00000002980232239 | 838,860,800 | 1,125,899,906,842,620 | 16,384 | 34,359,738,368 | 77,313,607,690 | 0.00048828125 |
| 51 | 1,125,899,906,842,620 | 0.00000001490116119 | 855,638,016 | 2,251,799,813,685,250 | 16,384 | 68,719,476,736 | 146,033,084,426 | 0.000244140625 |
| 52 | 2,251,799,813,685,250 | 0.000000007450580597 | 872,415,232 | 4,503,599,627,370,500 | 16,384 | 137,438,953,472 | 283,472,037,898 | 0.0001220703125 |
| 53 | 4,503,599,627,370,500 | 0.000000003725290298 | 889,192,448 | 9,007,199,254,740,990 | 16,384 | 274,877,906,944 | 558,349,944,842 | 0.00006103515625 |
| 54 | 9,007,199,254,740,990 | 0.000000001862645149 | 905,969,664 | 18,014,398,509,482,000 | 16,384 | 549,755,813,888 | 1,108,105,758,730 | 0.000030517578125 |
| 55 | 18,014,398,509,482,000 | 0.0000000009313225746 | 922,746,880 | 36,028,797,018,964,000 | 16,384 | 1,099,511,627,776 | 2,207,617,386,506 | 0.0000152587890625 |
| 56 | 36,028,797,018,964,000 | 0.000000000466 | 939,524,096 | 72,057,594,037,927,900 | 16,384 | 2,199,023,255,552 | 4,406,640,642,058 | 0.00000762939453125 |
| 57 | 72,057,594,037,927,900 | 0.000000000233 | 956,301,312 | 144,115,188,075,856,000 | 16,384 | 4,398,046,511,104 | 8,804,687,153,162 | 0.000003814697265625 |
| 58 | 144,115,188,075,856,000 | 0.000000000116 | 973,078,528 | 288,230,376,151,712,000 | 16,384 | 8,796,093,022,208 | 17,600,780,175,370 | 0.0000019073486328125 |
| 59 | 288,230,376,151,712,000 | 0.0000000000582 | 989,855,744 | 576,460,752,303,424,000 | 16,384 | 17,592,186,044,416 | 35,192,966,219,786 | 0.00000095367431640625 |
| 60 | 576,460,752,303,424,000 | 0.0000000000291 | 1,006,632,960 | 1,152,921,504,606,850,000 | 32,768 | 17,592,186,044,416 | 52,785,152,264,202 | 0.00000095367431640625 |
Glossary
Updated Apr 1, 2025
Accounting Entity - An Accounting Entity represents a set of books (accounting) for a Party. All [Conduit Network] rights, obligations, or value transfer transactions occur within the scope of an Accounting Entity for all counterparties (Parties) in a transaction. Each Accounting Entity supports order management and fulfillment for Resources, complete with inventory, purchase orders, sales orders, and invoicing, which are useful for tax, import, or export invoices.
Billing - Billing is the process of calculating a charge for the use, sale or transfer of a Resource, or a set of Resources, which can occur in real time, near time or be periodic based. Billing works hand and hand with Settlement which can be real time, near time or periodic as well.
Block of CNDT - An amount of CNDT that can be mined based on the Conduit Network mining schedule.
CNDT (Token) - The native token of the Conduit Network.
Conduit Core - A modular stack of network and computer hardware consisting of a Connectivity Module, a Security Module, and at least one Compute Module.
Conduit Network - Conduit Network is a computer network designed with decentralized opinions and an economic system implemented as a robust rewards program. Conduit Network provides a rich set of semantics and protocols designed to facilitate and foster economic activity in which all parties involved experience mutual benefit. The design of Conduit Network is based on three key tenets:
- Cost Reduction
- Mutual Benefit
- Decentralization
Conduit Node0 License - A license to operate a Worker Node at the Standard Trust Level, running a verified Worker Node OS on the Conduit Network.
Conduit NodeX License - A license to operate a Worker Node at the Enhanced Trust Level, running a verified Worker Node OS on the Conduit Network.
Conduit Rewards System - Conduit implements a multifaceted rewards system for many different types of participation in the network with the goal to create a secure decentralized network for both Web 2 and Web 3, owned by its operators, creators and users. How it works
CROP - CROP stands for Cost Reduction from (shared) OPerations representing efficiency increase in economic terms. CROP has two primary functions: it is a measuring tool and fund source. As a measuring tool it is an indicator of economic activity of a network as it is attached to every economic transaction in the network. As a fund source CROP creates a pool of resources to be used according to the Conduit Network Distribution Pools that incentivize shared operational efficiency in the network.
CROP Ledger - A ledger type specifically designed to track CROP contributions. These ledgers are utilized at a network and individual Party level. They keep track of a Parties CROP contributions, as well as the total Conduit Network CROP contributions. They inform Mining events for individual Parties and block releases and phase changes for Conduit Network.
Ecosystem - A mutual company, trade association or co-operative operated for the mutual benefit of its participants that uses the Conduit Network.
Enhanced Trust (Trust Level) - Enhanced Trust Nodes represent a compromise between Standard Trust and High Trust that attempts to find the sweet spot between cost and the friction of use versus the skill or economic cost of breaching security or violating trust. Enhanced Trust Nodes are only available from a list of qualifying hardware device manufacturers from third-parties that have been vetted. Enhanced Trust Nodes can be purchased directly from their suppliers and can be configured to operate within the Network or purchased pre-configured through the Conduit infrastructure Ecosystem. NOTE: In order to participate in economic activity a Enhanced Node must also have a Conduit NodeX License attached.
Event Proof - Proof of circumstances that can trigger:
- The Billings of one or more counter-parties for a Resource use, sale or transfer
- An exception or error handling routed for human inspection or automated intervention
- The triggering of another action
- The notification of one or more Parties or Agents.
Founders Edition - The inaugural manufacturing run of Conduit Core devices limited to 1,000 units.
High Trust (Trust Level) - Nodes that are appropriate for use in the most demanding trustless security environments including critical banking, nation state and utilities infrastructure. These Nodes can only be purchased through licensed Syndicates (a Network version of a DAO) within the infrastructure Ecosystem. These Syndicates must demonstrate that they maintain a fully audited supply chain that can provide full provenance for all components. All components that are deemed to pose a quantifiable risk must also come from Members of licensed Syndicates within the infrastructure Ecosystem. All hardware, OS and software for High Trust Nodes are designed by Conduit and only manufactured by licensed Parties who use approved suppliers for components. Software components can only be created and modified by licensed Parties and must be audited by licensed Parties. All hardware for High Trust Nodes that run Secure Core Services must be NIST rated to comply with the FIPS 140-2 (level 3) standards.
The entire supply chain for High Trust Nodes must ensure provenance and auditable history of each component. Any party who wishes to participate in building components for High Trust Nodes must go through a rigorous training process, risk assessment and submit to regular audit processes as well as agreeing to join a Syndicate that places the right to all IP used within a Network trust. Therefore, High Trust Nodes for use in the Network are only available through the Conduit infrastructure Ecosystem and must be purchased through Network websites or Apps.
Low Trust (Trust Level) - Nodes that are appropriate only when there is virtually no value to compromising the device or gaining access to information it contains or produces. Shared public information is a good example. Any hardware system can be considered a Low Trust Node. In fact, all non-verified Nodes in the Network are considered Low Trust Nodes until proven differently. This means that any device already owned or in use by anyone can be considered and used as a Low Trust Node. The Conduit infrastructure Ecosystem websites and apps do not offer any pre-configured Low Trust Nodes as their use is not encouraged by the Network. However, every hardware connected to the internet today and every cloud computing environment unless certified to a higher standard are considered Low Trust.
LP Entity - LP Entity is an authorized term given to a Participant that is licensed to conduct business activities and trade in the Conduit Network.
Member - A Participant in the network that has been through basic KYC.
Mining - Mining on the Conduit network is done by proving and tracking economic activity. The proving and tracking is done by contributions made on every economic transaction in the Conduit Network called CROP contributions.
Node - A Node is a compute resource that is connected to and resides on the the Conduit Network. Nodes can have different functions, operate in different capacities, and have differing Trust Levels.
Node0 License - A license to install and run the Worker Node OS on the Conduit Network on a Standard Trust hardware trust level or higher and participate in network economics.
Node Operator - The Party responsible for operating a node on the Conduit Network.
Participant - A Participant is any person or legal person taking action on or in the Conduit Network.
Party - A Party is a Participant or LP Entity. Each Party has at least one Accounting Entity which is the default root accounting entity for the Party.
Phase - A subdivision of the Conduit Mining Schedule based on the total amount of CROP contributed in the network. Phases establish the amount of Blocks released and the amount of CNDT in a Block.
Predicate - Predicates are made of boolean statements that use values stated in an object graph.
Predicate Proof - A cryptographic proof generated from Predicates. Can be specified as zero knowledge or transparent based on authority rights.
Resource(s) - A Resource is anything in the Network that has economic value. Resources are measured by Smart Meters that run on Worker Nodes running the Worker Node OS.
Secure Core Services - A common set of services that protect the network, enable data to be held in trustless and even hostile environments, route and broker the use of network resources, and handle all billing and transfer of value on the nework. These services include:
- Accounting, ledgers, key storage, secure storage and wallets
- Data replication, consensus and messaging
- Financial settlement, payments, blockchain bridges and tokenizable assets
- Identity, authentication, authorization and claims management
- Resource management, capacity, location, name resolution and routing
Security Module - The Conduit Security module is a computer that meets the High Trust hardware specification and runs the Conduit Secure Core Services.
Settlement - A concluded transfer of value. When something of value (for example, a right in or to a product or service) is transferred between two or more parties concurrent with a corresponding transfer of value (for example, usually a payment of cash, or cash together with Points) and which closes a receivable on a Sales Transaction, and thereby extinguishes a particular right, obligation and/or liability.
Smart Meter - Smart Meters perform two functions:
- The creation of Predicate Proofs upon a Predicate dictating a significant event
- Provide Billing information for use, sale or transfer of a Resource that Smart Meter monitors or measures to a Security Module to calculate the charge and do the Billing and Settlement.
Standard Trust (Trust Level) - Nodes that are appropriate for use where there is low value to someone gaining unauthorized access or for use where there may be economic loss but which would not be significant in either individual cases or the aggregate. Standard Trust Nodes may be able to be considered Enhanced Nodes when they exist in environments that have high physical and connectivity protection. For example, secure data centers or in private networks not connected to the internet. Standard Nodes can be supplied by many commodity hardware providers. Even legacy hardware that new Network Participants already own may qualify for use as a Standard Node. Standard Nodes can be purchased directly from their suppliers and can be configured to operate within the Network by installing the Worker Node OS. Also, a limited list of pre-configured Standard Nodes are available for purchase via the Conduit infrastructure Ecosystem websites and apps. These come with the Worker Node OS preinstalled. NOTE: In order to participate in economic activity a Standard Node must also have a Conduit Node0 License attached.
Syndicate - Syndicates are DAOs inside of an Ecosystem which means they function like a subcontractor in an Ecosystem. They are not legal entities themselves, rather a consortium governed by the Syndicate Governance under the Ecosystem Governance.
Temporal Ledger - A Temporal Ledger enables the recording of updates that supersede existing information, or to record transactions that occur on a future date and don’t require any additional processing to take effect. For example, a Party can change their address for example and have it go into effect in the future when they actually move. Temporal Rights Ledgers are one of the most fundamental differences between the Conduit Network and traditional blockchains because they solve custody problems.
Trust Levels (Hardware) - A hierarchy of states describing risk and levels of security.
Wallet - A storage mechanism for two types of accounts:
- Fungible - Accounts that hold asset classes that are freely exchangeable, such as gold, rice, cash, shares of stock in a specific company, etc.
- Non-fungible - Accounts that hold asset classes where each item is unique and can’t be exchanged one for another because the assets are not equivalent, such as real estate, vehicles and NFTs.
Worker Node - Any device that is used to measure the existence of or use or purchase of something of economic value, a resource.
Worker Node OS - A Linux based immutable operating system that uses Conduit Network authorizations and implements Smart Meters.
Disclaimer
This documentation is subject to change throughout the Conduit Network testnet phases.